
Catching Threat Actors using honeypots (part 2)
Table of contents
Introduction
Hi There! In my last post we set up a lot of honeypots. It’s time to harvest our first fruits! In this post, we will start to analyze some of our data collected. However, since we gathered around 20 GB of data already, I need to sort out a lot of information. If you are missing some information or context, feel free to let me know in the comments or via Discord. Enough of the talky, let’s dive into the data!
General data
Before we start looking at specific honeypot data, we should get a feeling for the bigger picture.
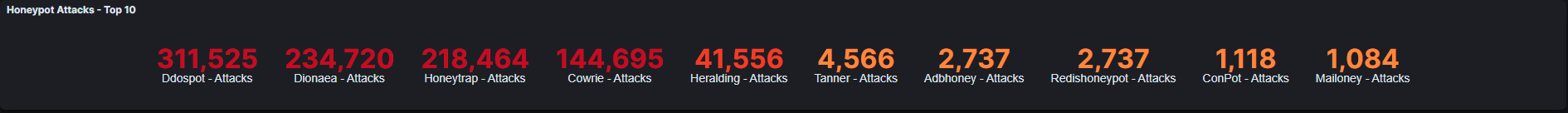
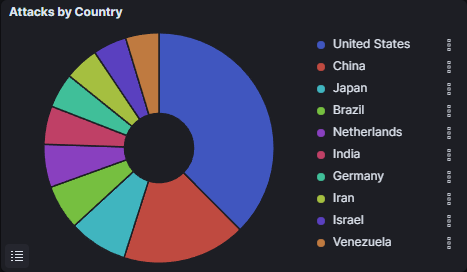
Considering the fact that we started our honeypots on the 6th of April we collected data on ~ 1,000,000 attacks! Our top talker is the ddospot. If you think about it, it’s not that surprising. DDoS is pretty much the lowest hanging fruit of attacks. All you have to do is craft a single packet/request and spam it to unlimited amounts of IP addresses. However, it’s not the most interesting honeypot for us, since the only cool thing we can collect are source IPs. Looking at one graph, something to look suspicious tho..
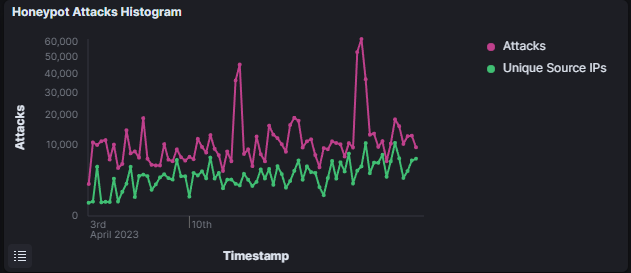
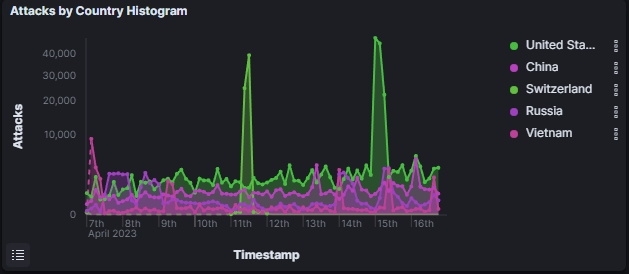
When we take a look at the attack over time Histogram, we can see 2 spikes. But what do they mean? My hypothesis so far: A larger botnet started scanning for new victims! Why do I think so? If we look at where the attacks came from, we can see that the attacks which led to the spikes came from Switzerland and the US.
Cowrie
Today I want to put the focus on our Cowrie honeypot.
What is Cowrie?
Cowrie is a highly customizable and configurable SSH honeypot designed to emulate a vulnerable Unix-like environment, in order to capture and analyze the behavior of attackers attempting to gain unauthorized access. Cowrie is written in Python and is available as an open-source tool, allowing users to tailor the honeypot to their specific needs. Cowrie includes a range of features and functionalities that make it a powerful tool for studying attacker behavior and techniques.
Cowrie can be configured to emulate various SSH services and protocols, including password and public key authentication, as well as different operating systems and software environments. The honeypot can also be configured to capture and log various types of data, including session output, keystrokes, and network traffic. Cowrie supports various logging formats, including JSON, CSV, and Syslog, making it easy to integrate with existing security and log management tools.
Cowrie also includes a range of plugins and modules that extend its functionality, such as the ability to detect and respond to port scanning and brute-force attacks. Cowrie can also be configured to integrate with external threat intelligence sources, allowing it to detect and respond to known attack patterns and malicious actors.
Lets look at the data..
Cowrie data
When we look at the attack map, we can clearly see our top talker is the US. This makes sense since we already saw a potential botnet attack from the US.
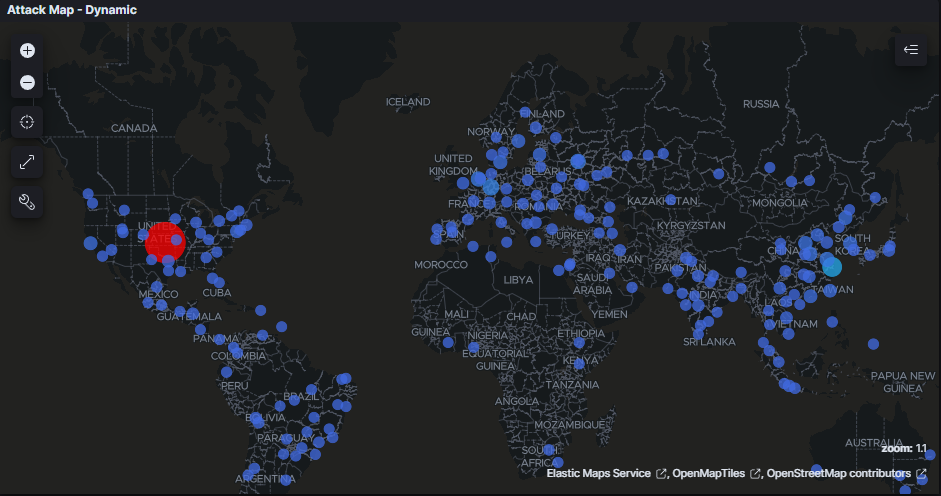
On the next graph, we can see the protocols and the countries from where the attack originates.
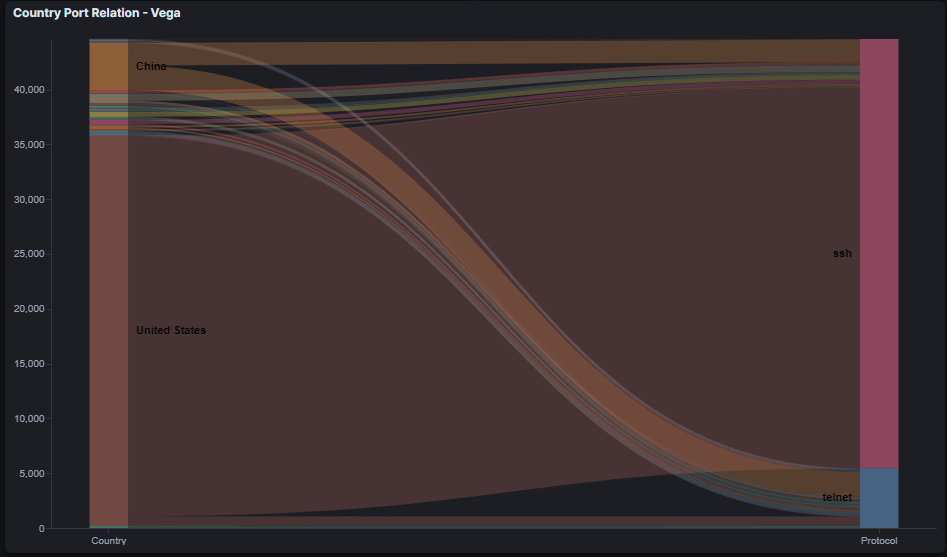
It’s interesting that we can see the telnet port being attacked. But why would attackers still attack this ancient protocol, when almost every system nowadays uses SSH?
Telnet vs SSH
Threat actors may prefer to target telnet instead of SSH because telnet is an older, less secure protocol that does not encrypt data sent over the network. Telnet was designed for remote access to command-line interfaces and was widely used in the early days of the internet. However, telnet does not use encryption or secure authentication mechanisms, which makes it vulnerable to eavesdropping, data interception, and password sniffing attacks.
In contrast, SSH is a newer, more secure protocol that encrypts all data sent between the client and server, making it much harder for attackers to intercept and exploit. SSH also supports a range of authentication methods, including public key authentication, which makes it much harder for attackers to guess or steal passwords. As a result, SSH is considered to be a more secure alternative to telnet, and is widely used in modern network environments.
However, there are still many legacy systems and devices that use telnet for remote access, and these systems may be vulnerable to attacks if not properly secured. Additionally, some attackers may prefer to target telnet because it is a known vulnerability, and there may be a larger pool of potential targets compared to SSH.
If you are dumb enough to still run telnet nowadays, you are most likely dumb enough to have a root:root credetential pair..
Credentials
Let’s look at the credentials the Threat Actors used to access our SSH/telnet honeypot.
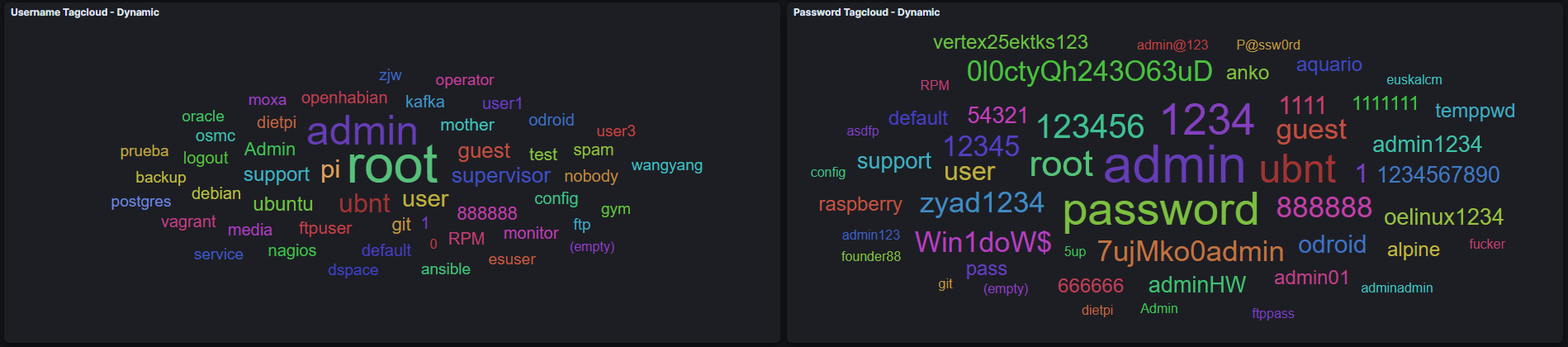
We can see the most obvious usernames like admin/root/guest and passwords like admin/password/root/1234 being used a lot to brute force our system. However, if you take a closer look, you can spot something weird..
One of the most used Usernames is “mother” and one of the most used password is “fucker”? There is a pretty good reason why those credentials are being used to brute force our system.
My educated guess so far is that IPs using these credentials to authenticate are bots created by the Threat Actors to sniff out honeypots! If you think about it, it’s quite obvious. SSH honeypots accept almost every credential pair as a valid login to lure in attackers. All you have to do is use a credential pair not a single sane person (beside League of Legends/Counterstrike players) would use. So why not use the credentials mother:fucker.. If you can authenticate with those credentials, you can be almost certain that you found a honeypot. Now you can blacklist it from your scans/attacks and hide from security researchers like me :-(
commands
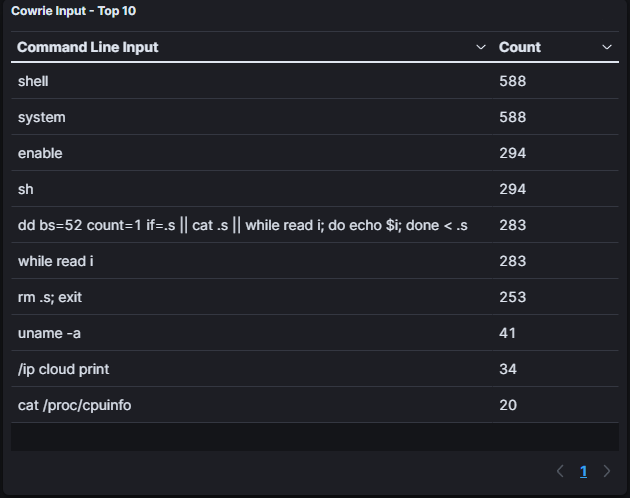
After the Threat Actors logged onto our honeypot, they see a shell and a file system. They don’t know that it’s all fake, tho. So what are the Threat Actors doing on the command line? The answer is simple.. System Discovery! Most of the time servers are being compromised to be part of a botnet. To deliver the right malware, Threat Actors need to know what hardware is running on the system. Especially the CPU infrastructure is interesting since malware often depends on specific CPU functions. Below, you can see the top 10 used commands:
malware samples
However, the Threat Actors do need to bring the malware on the system after successfully brute forcing it. So they download the malware from the CLI by using wget or cURL. Luckily, Cowrie saves a copy of every file downloaded to our honeypot! In the last 11 days, I collected 21 unique malware samples. That makes almost 2 unique malware samples A DAY! I uploaded all malware samples to my file server for you to do your own research. Enjoy!
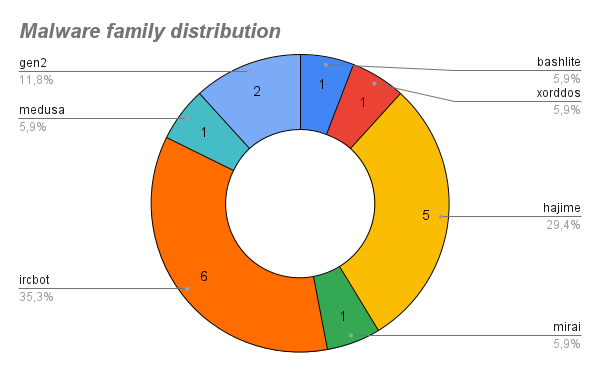
To give you a quick lecture on malware families I will give you a small summary on every malware found in my honeypots :)
IRCBot
IRCbot malware, also known as an Internet Relay Chat bot, is a type of malware that creates a backdoor in an infected system, allowing remote attackers to control the computer through an IRC channel. This malware typically spreads through phishing emails, malvertising, or software vulnerabilities. Once installed on a victim’s computer, IRCbot uses a range of techniques to evade detection, such as encrypting its code or hiding its presence.
IRCbot malware can be very damaging to a victim’s computer and personal data. It can be used to steal sensitive information, modify system settings, download and execute additional malware, or use the infected system as part of a botnet to carry out distributed denial-of-service (DDoS) attacks on other targets. To protect against this threat, it is important to keep antivirus software and operating systems up-to-date, use strong passwords and two-factor authentication, avoid downloading software or clicking on links from untrusted sources, and be cautious when opening email attachments or clicking on links in unsolicited messages.
Hajime
Hajime is a type of malware that targets Internet of Things (IoT) devices such as routers, cameras, and other connected devices. Unlike most other malware strains, Hajime is designed to secure and protect vulnerable devices, rather than exploit them for malicious purposes. Once installed on an IoT device, Hajime blocks access to known vulnerabilities and backdoors, making it harder for other malware to infect the device.
Hajime spreads through scanning for open Telnet ports on IoT devices and then attempting to brute-force the login credentials to gain access. The malware is designed to be stealthy and persistent, making it difficult to detect and remove. Hajime also uses a peer-to-peer network for communication between infected devices, allowing them to work together and share resources.
Although Hajime appears to have noble intentions of protecting IoT devices, its true purpose and origin remain unknown. As with any malware, it is important to take steps to protect against Hajime and other threats, including changing default passwords on IoT devices, updating software and firmware regularly, and implementing security controls such as firewalls and intrusion detection systems.
In my opinion it is also note-worthy to mention that is was found waaay more than Mirai samples. If you are interested in Mirai you can check out this post from me!
Medusa
Medusa malware is a type of Trojan that is designed to steal sensitive information and provide remote access to an infected system. Medusa typically spreads through phishing emails, software vulnerabilities, or malvertising. Once installed on a victim’s computer, the malware can perform a range of malicious actions, including stealing login credentials, financial data, or personal information.
Medusa is often distributed as a kit that allows attackers to customize the malware for their specific needs. The malware can be designed to evade detection by using techniques such as encryption, anti-analysis, or hiding its presence on the infected system. Medusa can also create a backdoor or remote access point on the infected system, allowing attackers to remotely control the computer and carry out further malicious activity.
XORDDoS
XorDDoS is a type of malware that is used to carry out distributed denial-of-service (DDoS) attacks against targeted websites or networks. The malware typically infects Linux servers through a vulnerability in the Apache Struts web application framework. Once installed on a victim’s server, XorDDoS creates a botnet of infected devices that can be used to flood a target website or network with traffic, effectively taking it offline.
XorDDoS is designed to be difficult to detect and remove. The malware can hide its presence on an infected system, making it hard to identify the source of the attack. Additionally, XorDDoS can use a range of evasion techniques, such as randomizing the source IP address of attack traffic, to make it harder for defenders to block the attack.
BASHLITE
Bashlite is a type of malware that targets Internet of Things (IoT) devices such as routers, cameras, and other connected devices. It is also known as Gafgyt or Qbot. Bashlite spreads by exploiting software vulnerabilities and weak passwords to gain access to IoT devices. Once installed on a device, Bashlite creates a botnet that can be used to carry out distributed denial-of-service (DDoS) attacks against targeted websites or networks.
Bashlite is designed to be stealthy and persistent, making it difficult to detect and remove. It can also be used to steal sensitive information, modify system settings, or download and execute additional malware. Bashlite is often distributed through malvertising, phishing emails, or by exploiting vulnerabilities in unpatched software.
Outro
What a ride! We need to crunch some numbers to understand the landscape, but with analyzing our Cowrie data we made a great first step into our data mining adventure :-)
Please let me know what kind of data you want to see in the next post. Till then I wish you all a fantastic time and thank you for your time!
Sayonara
Mateo
Disclaimer
Any knowledge and code published in this blog post are intended for academic and educational purposes only. The author does not assume any responsibility for the accuracy or completeness of the information provided, nor does the author guarantee that the code presented will function correctly. Any use of the knowledge or code provided in this blog post is solely at the reader’s own risk. The author shall not be liable for any losses, damages, or injuries arising from the use of the knowledge or code presented in this blog post. The reader is advised to exercise caution and consult appropriate resources before implementing any of the techniques or code presented in this blog post for any other purposes than academic and educational.
Supporters
I am incredibly grateful for the readers who have chosen to fund my blog and cyber security research. Your support allows me to explore new areas of research and contribute to the broader cyber security community. With your contributions, I am able to purchase necessary tools and resources (they can be pretty costy :-( ), attend conferences and training events, and collaborate with other researchers to produce valuable insights and findings. Thank you for your generosity and for joining me in this important mission.
List of Supporters:
- Junior-Ad
You can buy me a coffee here :-)