
Catching Threat Actors using honeypots! (Part1)
Introduction
Hey folks!
After a deep dive into reversing and analyzing one specific malware in the last blog post, I want to tackle a different topic today. To understand the landscape of Threat Actors nowadays, it is crucial to look at a huge data set. But how do we get those data sets? In my experience so far, high quality datasets are reserved for companies with $$$ to spend. However, as a poor security researcher, we can’t afford those datasets. We need to get creative. So, let’s just generate our own Dataset using honeypots!
This series will be split in about 3–4 Parts. In this one we will start of with the architecture and installation.
Table of Contents
- Introduction
- Introduction to honeypots
- Honeypot Architechture
- Installation
- T-Pot Handling
- Outro
- Disclaimer
- Supporters
Introduction to honeypots
Honeypots are a powerful tool for security researchers to gain insights into the latest attacker tactics and techniques. By setting up decoy systems that mimic real-world applications and services, security researchers can monitor attacker behavior in a controlled environment, without putting real systems or sensitive data at risk. Honeypots can be configured to attract different types of attackers, from script kiddies to advanced threat actors, and can be used to gather a variety of data such as IP addresses, malware samples, and command-and-control communications. By analyzing this data, researchers can gain a deeper understanding of how attackers operate, identify emerging trends, and develop effective countermeasures.
In addition to providing valuable intelligence on attackers, honeypots can also be used to test offensive capabilities and improve overall security posture. By deploying decoy systems with known vulnerabilities or intentionally weak security measures, researchers can identify weaknesses in their own defenses and prioritize remediation efforts accordingly. Honeypots can also be used to divert attackers away from valuable assets and reduce the risk of data loss or system damage.
However, it is important to note that honeypots are not a silver bullet solution to cybersecurity. They require careful planning and implementation, as well as ongoing maintenance and monitoring to ensure that they remain effective. Honeypots can also pose legal and ethical issues if not used appropriately, as they may attract malicious activity that could impact innocent third parties. Despite these challenges, honeypots remain a valuable tool for security researchers and can play a critical role in staying ahead of emerging threats.
However, in this blog post, we will talk about how to set up 20+ honeypots for almost no money!
Honeypot Architechture
To handle a large amount of honeypots all at once, we will use a project called “T-Pot”. T-Pot is an open-source honeypot platform that allows security researchers to easily deploy and manage a range of different honeypots on a single system. Developed by the German security company Deutsche Telekom AG, T-Pot provides a user-friendly web interface for managing honeypots, searching Data using ELK stack and storing logs using logstash. Here is an image of the T-Pot architecture:
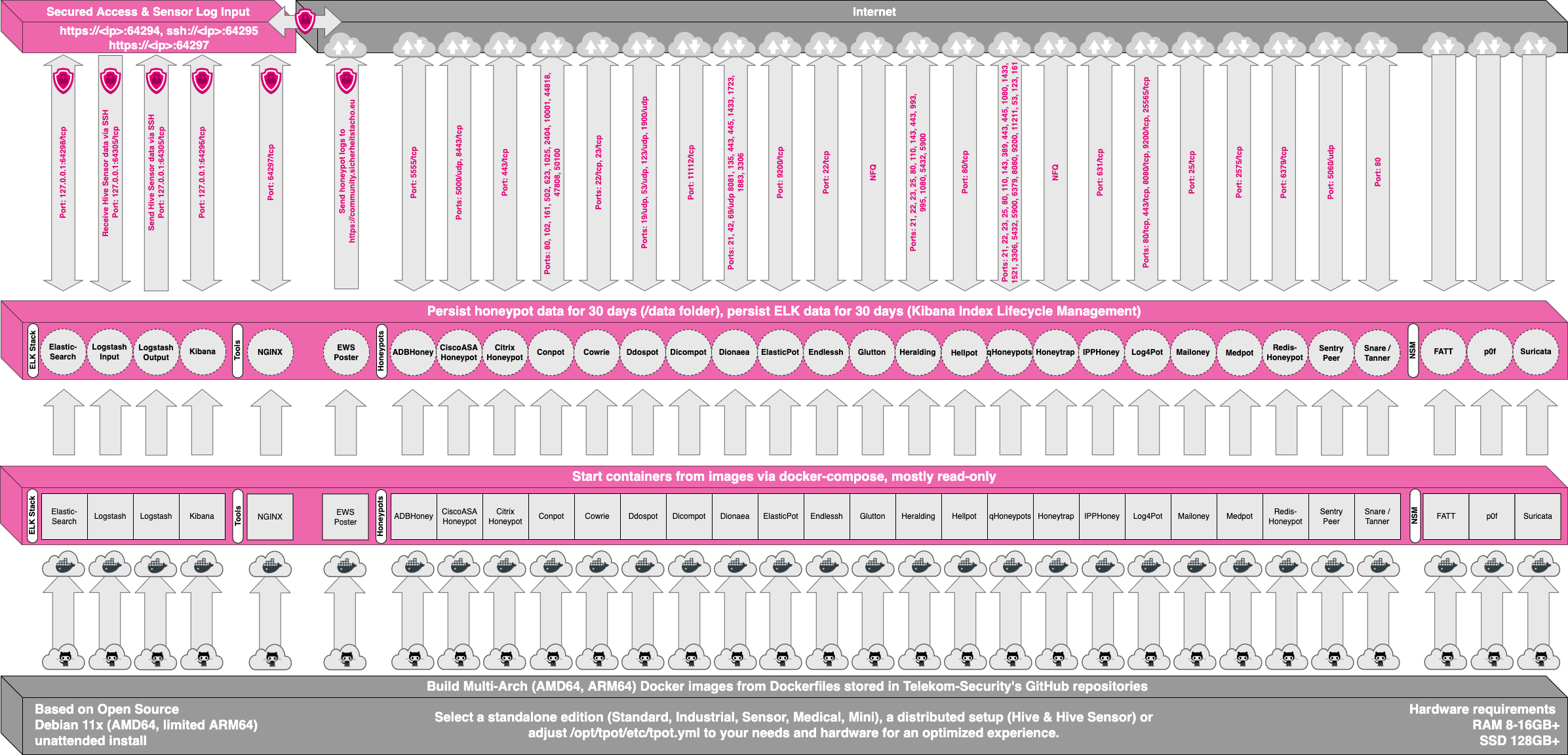
For now, we will take a closer look at the different honeypots available:
ADBHoney
Developed by the user “fs0c131y” ADBhoney is a honeypot designed to detect and analyze attacks against Android Debug Bridge (ADB) devices. ADBhoney works by mimicking a vulnerable ADB device, and logging any connections or commands sent to the honeypot.
CiscoASA Honeypot
CiscoASA Honeypot is a honeypot solution developed by Cisco Systems, designed to mimic the behavior of a Cisco ASA firewall in order to attract and monitor attackers.
Citrix Honeypot
Developed by Citrix Systems, the honeypot can be configured to emulate a variety of different Citrix environments, such as virtual desktop infrastructure (VDI) or application delivery controllers (ADCs).
Conpot
Conpot is an open-source honeypot platform designed to emulate industrial control systems (ICS) and SCADA protocols to detect and monitor attacks on critical infrastructure.
Cowrie
Cowrie is a popular open-source honeypot platform designed to mimic SSH and Telnet services, used to detect and monitor attacker activity. This one will be very interesting for us since it attracts A LOT of attacks.
DDoSPot
DDoSPot is a honeypot “platform” for tracking and monitoring UDP-based Distributed Denial of Service (DDoS) attacks. The platform currently supports the following honeypot services/servers in form of relatively simple plugins called pots:
- DNS server
- NTP server
- SSDP server
- CHARGEN server
- Random/mock UDP server
DICOMPot
Mimics a DICOM Server. DICOM is used for medical image transfer AFAIK.
Dionaea
Honeypot to mimick several different protocols. Here is a list:
- blackhole
- epmap
- ftp
- http
- memcache
- mirror
- mqtt
- mssql
- mysql
- pptp
- sip
- smb
- tftp
- upnp
ElasticPot
ElasticPot is an open-source honeypot platform designed to monitor and detect attacks on Elasticsearch instances, commonly used to store and search large amounts of data.
Endlessh
SSH honeypot designed to keep the threat actor’s connection alive as long as possible. Personally, I love the intention of this!
Glutton
Glutton is an open-source honeypot tool designed to emulate SMB file servers and collect information about attackers attempting to access and manipulate the decoy files.
Heralding
Simple honeypot to collect credentials. Implemented protocols:
- ftp
- telnet
- ssh
- http
- https
- pop3
- pop3s
- imap
- imaps
- smtp
- vnc
- postgresql
- socks5
Hellpot
Simulates a fake HTTP that tries to keep the connection alive as long as possible.
IPPHoney
Simulates a printer exposed to the internet.
Log4Pot
Simulates Log4Shell Vuln.
Mailoney
Mail honeypot simulating an open SMTP server.
Medpot
Honeypot emulating a HL7 / FHIR server. Those protocols are used in the medical field.
RedisHoneypot
Honeypot emulating a Redis server.
SentryPeer
I am pretty sure it’s a SIP honeypot collecting malicious IPs, Phone Numbers, etc.
TANNER
HTTP Honeypot.
Installation
Let’s talk about the installation of our honey pots. First, we need to think about the Infrastructure we are going to use. In T-Pots requirements, it says we need 16 GB of RAM and about 150 GB of SSD. A VPS with this size costs a small fortune and you’re bound to it for 6 months most of the time. To minimize costs, I decided to use vultr. With the referral code you should get 100$ free credits which should be enough for keeping this stuff up running for 30 days. The next step is to simply install the T-Pot ISO from this page.
After a successful Installation, when you go to http://your-server-ip:64297 you should see something like this.
Great! Our systems are ready to be attacked.
T-Pot Handling
Alright from the landing page we got some links to work with. To spoiler already: Only the links in the left box are relevant.
Cockpit
http://your-server-ip:64297/cockpit.html
Cockpit is a web-based GUI tool that allows system administrators to easily manage Linux servers from a web browser. It features a user-friendly interface for tasks such as monitoring system performance, managing users and services, and performing system-level tasks. Cockpit is lightweight, modular, and supports multiple authentication methods. It simplifies server management for system administrators who want to avoid using the command line. (Pretty uninteresting)
Cyberchef
http://your-server-ip:64297/cyberchef/
Cyberchef is the Swiss army knife of CyberSec tools. From Input Conversions to encryption, CyberChef got a tool for everything. I would strongly recommend you always having a CyberChef instance running.
Elasticvue
http://your-server-ip:64297/elasticvue/
Elasticvue is a free and open-source desktop application that provides a user-friendly interface for developers and system administrators to manage and visualize data in Elasticsearch. It simplifies tasks such as querying data, creating and managing indexes, analyzing data with visualizations, and monitoring cluster health. Elasticvue offers autocomplete search queries, drag-and-drop data manipulation, and real-time data visualization, making it a valuable tool for working with Elasticsearch data. (We won’t use this one)
Kibana
http://your-server-ip:64297/kibana/
Kibana is a free, Open-Source Web GUI to search your data. This will be our bread and butter for this project. However, the T-Pot devs are an absolute blast. For every honeypot, they implemented a dashboard already! All you have to do is navigate to http://your-server-ip:64297/kibana/app/dashboards#/ eh Voilà.
Here is a screenshot of the T-Pot main dashboard
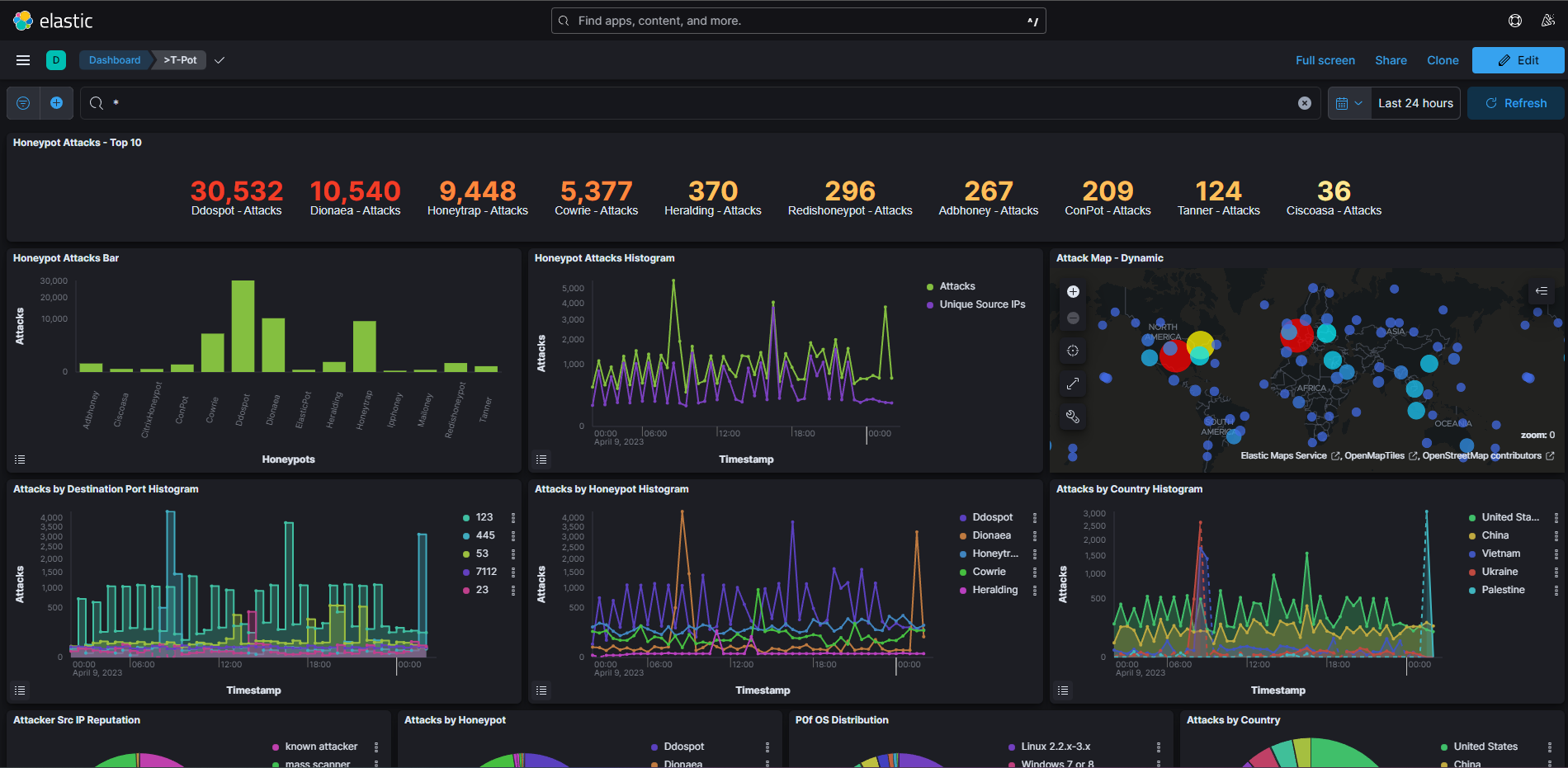
Spiderfoot
Spiderfoot is an amazing piece of CyberSec art. In a nutshell, SpiderFoot is an open-source tool that automates the process of collecting information from various internet sources to identify potential security risks. It can scan domains, IP addresses, emails, social media profiles, and more, and collect data from search engines, social media platforms, DNS records, and more. SpiderFoot can be used via command line or web interface, and its modular architecture allows for customization and easy extension. It helps security professionals and researchers identify threats and vulnerabilities to mitigate them.
Outro
Alright, so we got everything set up and got a feel for the tools. So good so far! In the next part, we will deep dive into the data and start exploring the attacks occurring on our honeypots. So far, I wish you all a good time and stay safe!
Sayonara
Mateo
Disclaimer
Any knowledge and code published in this blog post are intended for academic and educational purposes only. The author does not assume any responsibility for the accuracy or completeness of the information provided, nor does the author guarantee that the code presented will function correctly. Any use of the knowledge or code provided in this blog post is solely at the reader’s own risk. The author shall not be liable for any losses, damages, or injuries arising from the use of the knowledge or code presented in this blog post. The reader is advised to exercise caution and consult appropriate resources before implementing any of the techniques or code presented in this blog post for any other purposes than academic and educational.
Supporters
I am incredibly grateful for the readers who have chosen to fund my blog and cyber security research. Your support allows me to explore new areas of research and contribute to the broader cyber security community. With your contributions, I am able to purchase necessary tools and resources (they can be pretty costy :-( ), attend conferences and training events, and collaborate with other researchers to produce valuable insights and findings. Thank you for your generosity and for joining me in this important mission.
List of Supporters:
- Junior-Ad
You can buy me a coffee here